Microsoft NTLM is the default authentication protocol used on NT 4.0 and earlier Windows versions, now it was replaced with Kerberos ticket-based authentication protocol.
Two vulnerabilities CVE 2019-1166 and CVE-2019-1338 discovered in Microsoft NTLM allows attackers to bypass the MIC protection and modify the NTLM message flow along with signing requirement.
Microsoft fixed the released patch for the two vulnerabilities as a part of patch Tuesday for October. the vulnerabilities were discovered by Preempt researchers Yaron Zinar and Marina Simakov.
NTLM Attack Surface
NTLM is the most prevalent attack among Active Directory infrastructure, to mitigate the attack defenses such as NTLM relay signing and Enhanced protection in place to protect from NTLM relay attacks.
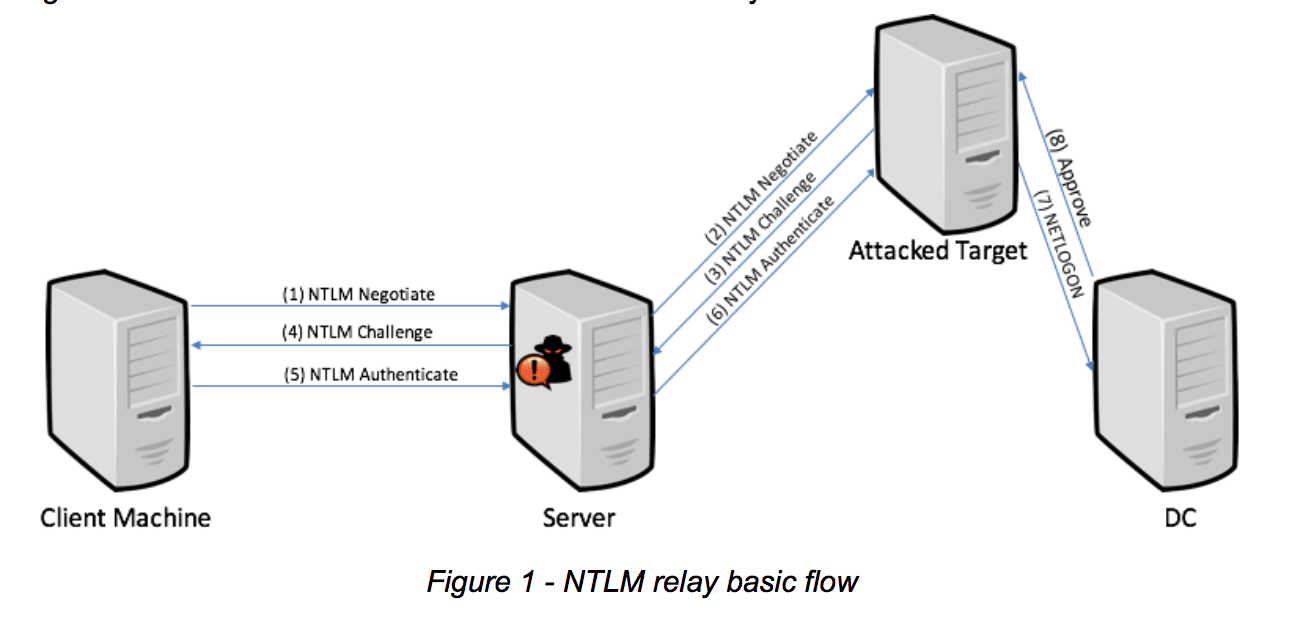
The MIC (Message Integrity Code) protection that ensures the attacker doesn’t tamper NTLM messages when the MIC is used with NTLM launching relay attack is difficult.
With CVE-2019-1166, researchers able to bypass the MIC protection, overcoming the fix for a previously disclosed vulnerability. In CVE-2019-1338, researchers able to bypass MIC along “NTLM relay mitigations such as EPA and the GPO for SPN target name validation for clients which add an LMv2 response to their NTLM authentication.”
Tampering Vulnerability
With the previous disclosure vulnerability CVE-2019-1040, they found a way to remove MIC messages without tampering the ‘msvAvFlag’ field.
Now they found an additional method to trick the server in believing that message doesn’t include MIC and they can modify the message at any stage of NTLM authentication flow.
“The key to this new vulnerability is the understanding that the MIC is an optional field and the only way NTLM servers can validate that this field is present is by inspecting the flags in the ‘msvAvFlag’ field. However, there is still a way they can bypass the MIC protection and modify any part of the NTLM negotiation stage, such as the signing requirement,” reads the report.

The EPA bypass vulnerability allows attackers to inject a ‘msvAvFlag’ into the av_pairs with the target field of NTLM_CHALLENGE and echo backed in NTLM_AUTHENTICATE message.
“We believe that this is a serious attack, as it adds unnecessary risks to SMB relay in most networks and those risks are further compounded with the additional danger of bypassing EPA in certain NTLM clients.”
Exploiting LMv2 Response
The vulnerability relies on the fact that the target server relies based on the NTLMv2 response and the Domain controller relies only on LMv2 and it doesn’t valid NTLMv2.
In this case “relayer can target clients which send both LMv2 & NTLMv2 responses, and modify any part of the NTLMv2 response when relaying the authentication against the attacked target.”
The attack leads to the full domain compromise of a network, the AD servers with default configurations are vulnerable to attack.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
