Hackers exploiting the recently disclosed Oracle WebLogic Server remote code execution vulnerability to install a new variant of ransomware called “Sodinokibi.”
The vulnerability allows anyone with HTTP access to the server can carry out the attack without authentication. The vulnerability affects Oracle WebLogic Server, versions 10.3.6.0, 12.1.3.0, Oracle fixed the issue on April 26, and assigned it CVE-2019-2725.
According to Talos Investigation, the initial stages of attack performed on April 25, on the same day where the Oracle released the patch. On April 26 attackers establish a connection with different vulnerable HTTP servers.
Attackers leverage the vulnerability to download the ransomware copy from attackers controlled servers and they also infected some legitimate sources and repurposed it.
“Cisco IR Services and Talos observed the attack requests originating from 130.61.54[.]136 and the attackers were ultimately successful at encrypting a number of customer systems.”
The infection starts with the HTTP POST request which contains the PowerShell or certutil command to download the malicious files and execute it.
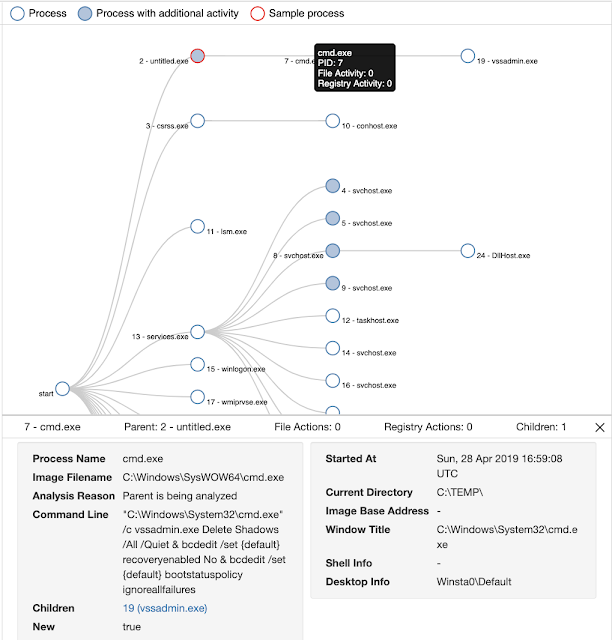
Once the infection triggered it executes the vssadmin.exe utility which adds shadowstorage that allows Windows to create a manual or automatic backup. The ransomware tries to delete the backup mechanism to stop the data recovery process.
The Ransom note directs victims to the .onion website and to a public domain (decryptor[.]top) which was registered on March 31.
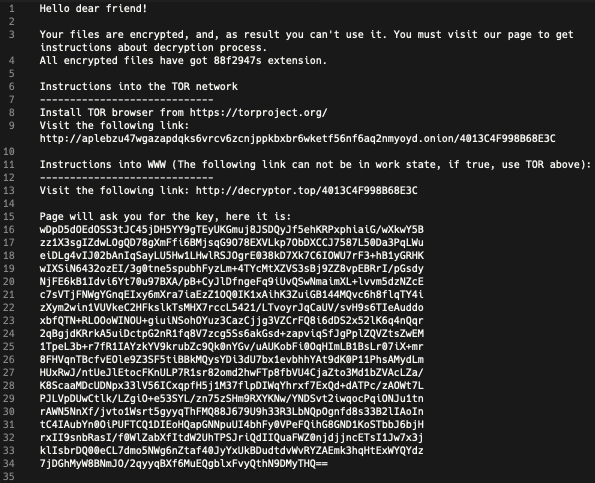
The visited website asks victim’s to buy a decryptor software to decrypt the files. In order to buy it, victims to create a Bitcoin wallet and buy Bitcoin worth $2500. Then the bitcoins need to be transferred to attackers wallet address to download the decryptor software. Also, they avail an option to test the decryptor tool by uploading an encrypted image.
After Sodinokibi ransomware deployment attackers chose to distribute Gandcrab v5.2 again to the same victim, thinking their earlier attempts had been unsuccessful.
It is recommended to patch the CVE-2019-2725 vulnerability, you can find the security alert published by Oracle and the Patch Availability here.
Indicators of Compromise
Ransomware samples:
0fa207940ea53e2b54a2b769d8ab033a6b2c5e08c78bf4d7dade79849960b54d
34dffdb04ca07b014cdaee857690f86e490050335291ccc84c94994fa91e0160
74bc2f9a81ad2cc609b7730dbabb146506f58244e5e655cbb42044913384a6ac
95ac3903127b74f8e4d73d987f5e3736f5bdd909ba756260e187b6bf53fb1a05
fa2bccdb9db2583c2f9ff6a536e824f4311c9a8a9842505a0323f027b8b51451
Distribution URLs:
hxxp://188.166.74[.]218/office.exe
hxxp://188.166.74[.]218/radm.exe
hxxp://188.166.74[.]218/untitled.exe
hxxp://45.55.211[.]79/.cache/untitled.exe
Attacker IP:
130.61.54[.]136
Attacker Domain:
decryptor[.]top
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity courses online to keep your self-updated.
Here you can find the Ransomware Attack Response and Mitigation Checklist.



.png
)
