A financially motivated hacking group called “GOLD SOUTHFIELD” launch a newly developed REvil Ransomware (aka Sodinokibi) which used the GandCrab ransomware code and infected the Windows users around the world.
Threat actors are distributing it through various medium including software installers with backdoor capabilities, exploit kits, exploiting RDP servers, and scan-and-exploit techniques.
Malware developers behind the GandCrab ransomware declared that they were shutting down its operations after earning $2 billion in ransom payments and security software maker Bitdefender released a free decryption tool for GandCrab.
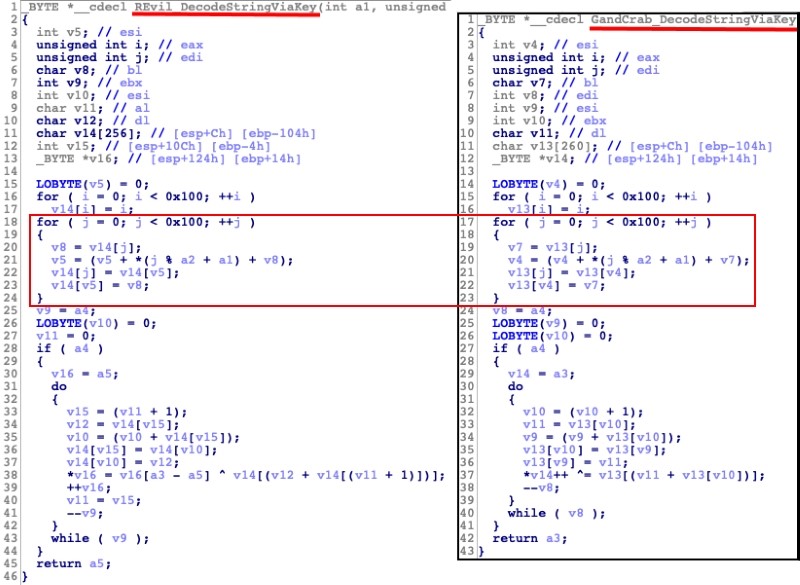
During the time interval, researchers from Secureworks learning the spikes of REvil ransomware and indented that REvil is likely associated with the GandCrab ransomware by having evidence of sharing its code.
REvil can perform a variety of malicious tasks, including the following,
1.Exploit the CVE-2018-8453 vulnerability to elevate privileges
2.Terminate blacklisted processes prior to encryption to eliminate resource conflicts
3. Wipe the contents of blacklisted folders
4. Encrypt non-whitelisted files and folders on local storage devices and network shares
5. Exfiltrate basic host information
REvil Ransomware Infection Process
Researchers learned that the first stage of REvil ransomware infection starts by exploiting the Oracle web logic servers, but later threat actors expanded their infection process via spam email campaign RDP attacks.
Some of the recent reports indicate that the REvil ransomware distributing by compromising the Italian WinRAR website and replace the malicious executable with a legitimate one and another scenario states that, it compromised MSP service provides and deploy the customer’s system.
Encryption Flow
During the encryption routine, REvil resolves the system library functions and compare with REvil binary to evade evades detection via static analysis and attempt to create a mutex .
If it is successfully created, REvil attempts to elevate privileges using an LPE exploit and execute either 32-bit or 64-bit shellcode based on the victim’s machine architecture.
Later it attempts to exploit the CVE-2018-8453, a Win32k Elevation of Privilege Vulnerability that allows an attacker to run arbitrary code in kernel mode.
REvil aka Sodinokibi already attempted to exploit this vulnerability in July, and infect the victims were located in the Asia-Pacific region: Taiwan, Hong Kong, and South Korea.
According to SecureWorks research ” REvil performs another privilege-related validation within its main function prior to profiling host information. If REvil’s current process is running with system-level integrity, then the process attempts to impersonate the security context of the first explorer.exe process it finds running on the compromised system. “
During the preparation for encryption, it generates, unique ID (UID), encryption keys and generate the random file extension and store the Base64-decoded ransom note template in nbody key of REvil’s configuration.
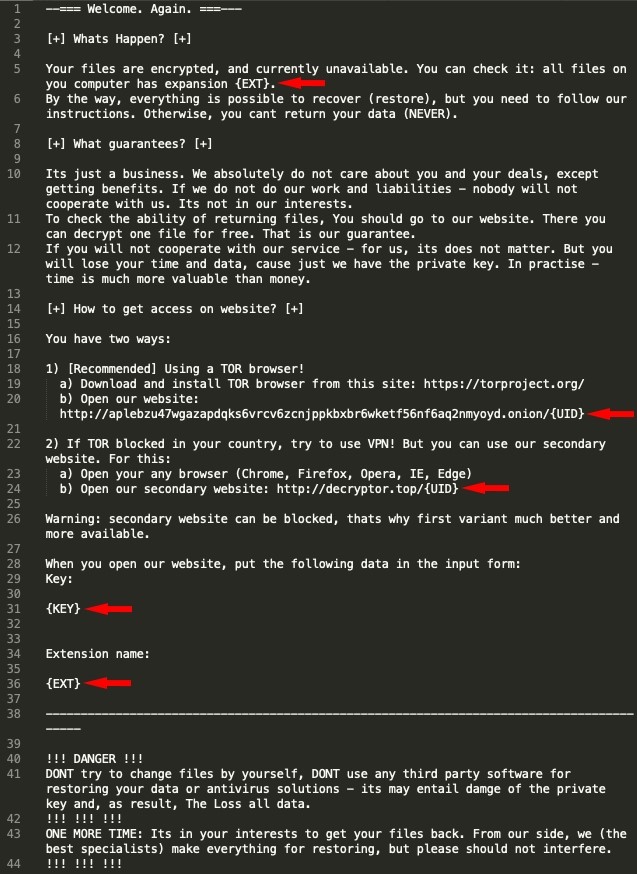
To obtain the decryption key from attackers, victims need to pay 0.203194 (roughly 2,300 USD) bitcoin within 4 days, if it failed then the ransom amount will be increased.
The analyzed sample requested that payment be sent to the Bitcoin address 3E9F7gE3upQ8rgsPjwiKH7ugfdneypPjqj, and there is no payment received for this wallet so far.
“Given the diverse and advanced delivery mechanisms, code complexity, and resources utilized by REvil, CTU researchers assess that this ransomware will replace GandCrab as a widespread threat. ” Secureworks concluded.
You can also read the “Ransomware Attack Response and Mitigation Checklist” to prevent yourself from the ransomware attack.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.



