GitHub has leaped application security by introducing a new feature that promises to revolutionize how developers address code vulnerabilities.
The new tool, code scanning autofix, is now available in public beta for all GitHub Advanced Security customers, harnessing the power of GitHub Copilot and CodeQL to offer unprecedented assistance in code remediation.
Found Means Fixed: A Vision for Application Security
GitHub’s vision for application security is encapsulated in the principle that “found means fixed.”
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
With the introduction of code scanning autofix, GitHub is making strides towards an environment where the discovery of a vulnerability is immediately followed by its resolution.
This tool is not just a theoretical advancement; it is a practical solution that has been shown to help teams remediate issues up to seven times faster than traditional security tools.
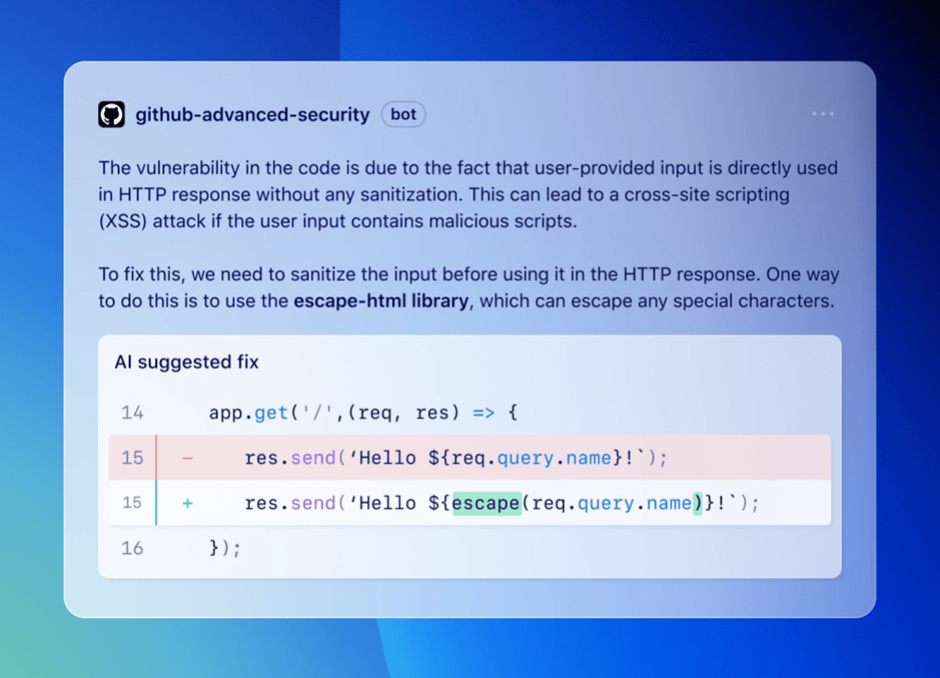
How Code Scanning Autofix Works
Code scanning auto-fix is designed to provide developers with an explanation and code suggestions to remediate a vulnerability.
This feature covers over 90% of alert types in popular programming languages such as JavaScript, TypeScript, Java, and Python.
It can deliver code suggestions that can remediate more than two-thirds of found vulnerabilities with minimal editing required by the developer.
Addressing Application Security Debt
Applications are a leading attack vector, and many organizations acknowledge the challenge of managing an increasing number of unremediated vulnerabilities in production repositories.
Code scanning autofix aims to curb the growth of this “application security debt” by simplifying the process for developers to fix vulnerabilities as they arise during coding.
Just as GitHub Copilot has been assisting developers by automating tedious and repetitive tasks, code scanning auto-fix is set to help development teams save valuable time previously spent on remediation.
Security teams also benefit from this tool as it reduces the volume of everyday vulnerabilities, allowing them to concentrate on higher-level strategies to safeguard the business in a fast-paced development environment.
The Technology Behind Autofix
The magic behind code scanning auto-fix lies in the CodeQL engine, which, in combination with heuristics and GitHub Copilot APIs, generates code suggestions.
When a vulnerability is detected in a supported language, the tool provides a natural-language explanation of the fix and a preview of the code suggestion.
Developers can then choose to accept, edit, or dismiss the suggestion. These suggestions can span multiple files and include necessary changes to project dependencies.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.



.webp)






