Researchers discovered a new trojan Masad Stealer to deliver the powerful spyware on the targeted systems and exfiltrate the stolen data via Telegram.
Masad Stealer using Telegram as a command and control channel to maintain the anonymity and hide the malware communication traffic.
Recent pas, several hacking groups are abusing the Telegram and used it as a part of their attack in different categories of a malicious campaign.
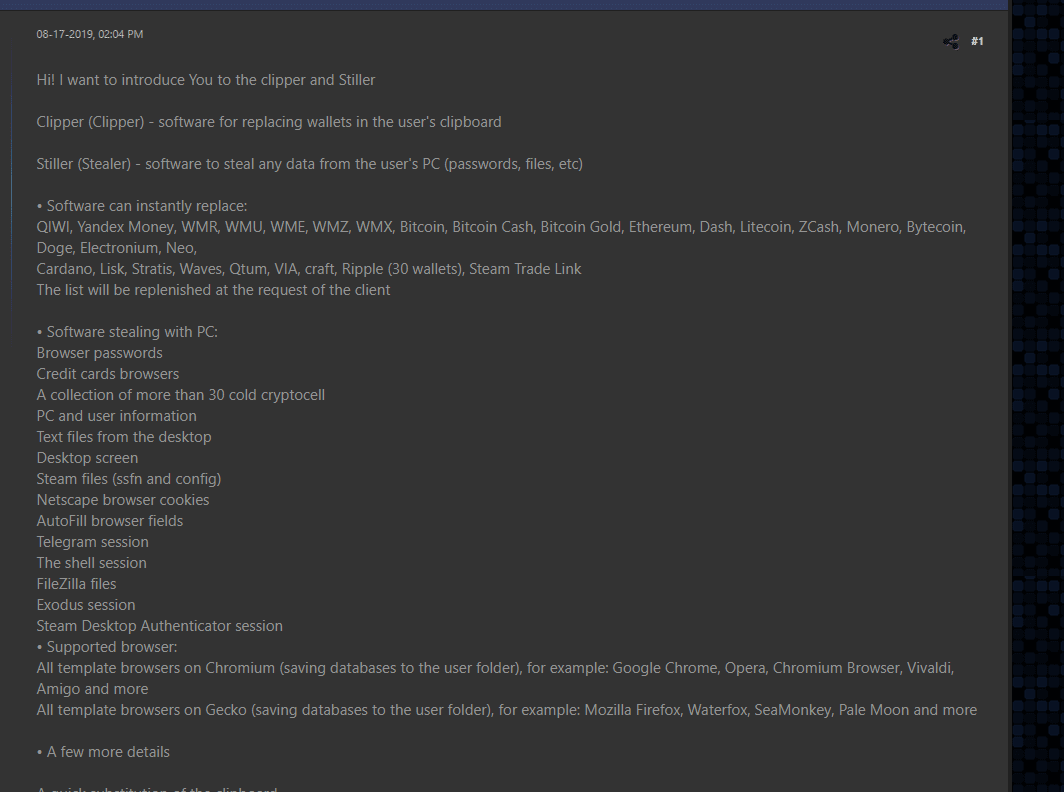
Malware developers who behind the Masad Stealer advertised in the underground hacking forums as it is capable of steals browser data, which might contain usernames, passwords, and credit card information.
Also, it automatically replaces the own cryptocurrency wallets from the clipboard with the help of Telegram bot that controlled by the attacker behind the scene.
Researchers believe that Masad Stealer is currently an ongoing campaign and actively attacking the thousands of victims around the world. also, the command and control bot still alive at this time of writing.
“This malware is being advertised in several hack forums as Masad Stealer. It starts with a free version and ladders up to versions asking up to $85, with each tier of the malware offering different features.”
Masad Stealer Infection Process
Malware authors using Autoit script to write this malware and later compiled as a Windows executable. Once it’s executed by users, it drops itself in %APPDATA%\folder_name}{file_name}, and create a scheduled task to restart itself in every one minute.
Once it confirms the successful installation, it attempts to collect the various sensitive information of the following.
- Cryptocurrency Wallets
- PC and system information
- Credit Card Browser Data
- Browser passwords
- Installed software and processes
- Desktop Files
- Screenshot of Desktop
- Browser cookies
- Steam files
- AutoFill browser fields
- Discord and Telegram data
- FileZilla files
After complete the data collection, it zips all sensitive data and bundles into malware binary.
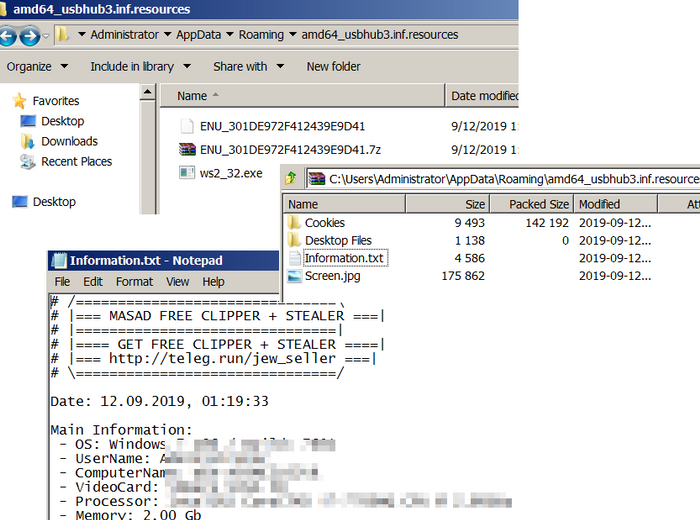
According to Juniper research, “This malware includes a function that replaces wallets on the clipboard, as soon as it matches a particular configuration. Below are the regular expressions and supported wallets that it matches against the clipboard data.”
Masad Stealer keeps checking its bot whether it is alive or not by sending a getMe message using the bot token and the bot reply back to the malware with the user objects that contains a user name of the bot.
Masad Stealer using a variety of the method as a distribution vectors such as advertising in forums, third-party download sites or on file-sharing sites.
Juniper researcher warned with the list of legitimate software such as CCleaner.exe, Iobit v 1.7.exe , Whoami.exe, Galaxy Software Update.exe and more are mimicked by Masad Stealer and trick victims to download and install it.
Malware authors also maintaining a dedicated website (masadproject[.]life) and Telegram channel with 300 members for their clients to promote the Masad Stealer and offer tech support.
Indicators of Compromise
SHA256
- e968affb1fc7756deb0e29807a06681d09a0425990be76b31816795875469e3d
- 4b1ccf6b823ee82e400ba25b1f532cd369d7e536475a470e2011b77ffeaf7bb3
- fc84d6636a34ad1a11dbaa1daec179e426bdcd9887b3d26dc06b202417c08f95
- 9ca15f15fbae58cb97b0d48a0248461e78e34e6d530338e3e5b91f209a166267
- 31f3a402c1662ed6adffbf2b1b65cf902d1df763698eb76d21e4e94b4c629714
- 8d9f124ddd69c257189f1e814bb9e3731c00926fc2371e6ebe2654f3950ca02e
- a0923d7645604faaa864a079adeb741a5d6e65507a2819b2fee4835d396077d9
- a19b790ea12f785256510dde367d3313b5267536a58ca0c27dbdac7c693f57e1
- f030fb4e859ee6a97c50c973a73dced3640befe37f579cfd15367ce6a9bbede2
- f01db6d77ac21211992ceae4e66e1e03c1cb39d61e03645b9369f28252ca7693
- dfe3d0e95feaed685a784aed14d087b019ba2eb0274947a840d2bdbae4ae3674
- bf6083040ca51e83415f27c9412d9e3d700bd0841493b207bc96abf944ab0ca7
- b154151dc8ace5c57f109e6bb211a019db20c4f0127c4d13c7703f730bf49276
- 6bf6b1bde63cee9b81902efd187fdd56ecee5853754ce0a19d5ab5c3b0242988
- 0dcf547bd8f4074af97416d8b84ea64b2f3319064aa4bce64ad0c2e2d3957175
- 6cff1249cc45b61ce8d28d87f8edc6616447e38168e610bed142f0b9c46ea684
- 5b5ebe019806885bbaafe37bc10ca09549e41c240b793fd29a70690a5d80b496
- 103d87098c9702cab7454b52869aeeb6a22919f29a7f19be7509255ce2d8c83e
- c73675005a09008bc91d6bc3b5ad59a630ab4670dca6ac0d926165a3ecfd8d92
- ef623aadd50330342dc464a31b843b3d8b5767d62a62f5e515ac2b380b208fbe
- 3ba3c528d11d1df62a969a282e9e54534fb3845962672ad6d8bbc29cb6d062f5
- b763054180cd4e24c0a78b49055ad36dbc849f1a096cddf2db8cee0b9338c21d
- d5ce4b04b7eec6530a4a9d40510177468fadc235253e5a74530a8c9d990f3c50
- 965a5949d8f94e17ebcd4cb6d0a7c19f49facbfc1b1c74111e5ceb83550d6c8f
- 44134b9d4b10d94f6381b446a1728b116d62e65c1a52db45235af12caf7e38c0
- 848d76a227f4fe282b7ddfd82a6dfc4c25da2735a684462b42fe4e1c413d8e34
- 5ca0a957fe6c253827f344da4ba8692d77a4e21a1df4251594be2d27d87dd8ae
- 016fa511f6546ed439d2606c6db8821685a99f5a14ef3f710668b58dc89c6926
- 22be594fbfa878f631c0632f6c4d260b00918817ff66a1f9f15efe44c1a58460
- f3571ec66288405dab43332ca03812617f85fb08832fbbe1f1d89901fe034b8a
- 04c949eca23103b1de05278b49f42c3ab6b06f4bf20aafa5f2faefaa84c16ecd
- e968affb1fc7756deb0e29807a06681d09a0425990be76b31816795875469e3d
- d6fc04acda8f33a6d35eb577c27754c2f2b4d6f4869576c7c4e11b2c5e9b0176
- 18c0bd4dd98008383fc52045ad896449fa7f0037593bb730ed1ef88aa547006d
- 4c9d5469e9095813418260045c2b11e499e4eaa0ffb25293f90f580c464157df
- 0b5f1fbc05dc8baca492b748adeb01fb4904e02723b59211ecde222f7b12d91e
- 31ad5c4547ceae4d0550c8460524c16a6105afc056760e872c4966656256c9dc
- edb00a0e5ff70e899857549e3263c887a799416c8bbab43ab130ca1be9bbd78c
- 96f852b81760a425befaa11ea37c0cdea2622630bf2a0c94bb95042211ab614d
- 57fd171a5b1a88e9583b42439851a91a940eb31105ab29cb314846da2ed43b82
- 277018b2cc6226dca6c7678cac6718c8584f7231340ad8cd7c03477559fdf48b
- 1acf5a461ee16336eb8bbf8d29982c7e26d5e11827c58ca01adac671a28b52ad
- 290a1b89517dec10bfd9938a0e86ae8c53b0c78ed7c60dc99e4f8e5837f4f24a
- 7937a1068f130a90b44781eea3351ba8a2776d0fede9699ba8b32f3198de045b
- 87e44bca3cc360c64cc7449ec1dc26b7d1708441d471bf3d36cd330db3576294
- cf97d52551a96dacb089ac41463d21cab2b004ba8c38ffc6cb5fb0958ddd34db
- 79aa23c5a25c7cdbaba9c6c655c918dac3d9823ac62ebed9d7d3e94e1eaafc07
- 03d703f6d341be258ac3d95961ff0a67d4bf792f9e896530e193b091dca29c2e
- a368b6755e62e5c0ff79ea1e3bd146ee8a349af309b4acf0558a9c667e78293a
- ba933cefbe9a8034f0ba34e7d18481a7db7451c8ef4b6172fb0cad6db0513a51
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.



.png
)